Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124

All people understand the essential importance of safeguarding their homes along with their loved ones. That’s why we’re eager to share our insights on biometric technology and personal security. Biometric devices offer a new level of security and peace of mind.
We’ll look into different personal security solutions like fingerprint, facial, and iris scanning. These use advanced biometric technology for top-notch security.

Our aim is to teach readers about the perks of using biometric devices for security. This piece provides an extensive review of existing choices. We’ll also highlight the latest in biometric technology and personal security solutions. Here We and Our Team Experts Got Solution For The Most Query Question Of “Biometric Device for Personal Security”
As we explore personal security, biometric authentication plays a key role. The technology shields both our personal identity information and our possessions from unauthorized access points. People are adopting this technology because it represents a secure method of information protection that simplifies security processes.
Biometric authentication uses unique traits like fingerprints, facial recognition, or voice to confirm who we are. The new approach to security through this method improves safety while reducing inefficient practices. Assets together with personal information remain protected from unauthorized access through this security measure.
Biometric security has many benefits. Biometric security increases safety by creating another protection barrier that safeguards users from scam and identity theft crimes. Biometric security provides users with security systems that are convenient to use and friendly to operate. As we move forward, biometric technology will likely play a bigger role in security.
Some key benefits of biometric security include:
Understanding biometric authentication and its role in personal security is crucial. The high importance of this technology for identity protection and asset ownership is plainly demonstrated. As we delve deeper into biometric security, its impact on future personal security will be significant.
We’re excited to look at the different biometric devices out there. These include fingerprint recognition, facial recognition, and iris scanning. Biometric authentication solutions provide two main advantages of enhanced protection together with user convenience.
Some top biometric devices are:
These technological devices find applications in personal security needs as well as business environments. Fingerprint security technology serves as an additional protection system within modern smartphones and laptops. Facial recognition is used at airports to check identities and stop fraud.

Biometric devices are also used in other ways, like:
In summary, biometric devices These security systems increasingly become popular because they provide multiple advantages. Security improves as well as users experience convenience and enhanced ease of use. The implementation of fingerprint and various biometric technologies brings about safer and more efficient systems.
We search for fingerprint recognition systems that are accurate, easy to use, and affordable. Personal security heavily relies on this technology. The following section presents our selection of fingerprint recognition systems which include commercial and consumer-level options.
Our organization has examined multiple finger print systems for evaluation purposes. We evaluated the devices according to their precision levels together with their usability features and cost-effectiveness. Our objective directs you toward selecting the most dependable security solution. Here We and Our Team Experts Found Information About Query Question Of “Find the Best Smart Glasses: Our Expert Picks“

Commercial grade biometrics are perfect for businesses. They offer advanced security features. Key features include:
People use consumer-level systems for their personal needs. Consumer-level systems enable users to safely protect their devices through straightforward operation.
Some popular options are:
Many options from the commercial sector and consumer market combination enable us to identify the suitable system for our requirements and financial constraints.
We’re excited to dive into the newest in facial recognition tech, a big part of biometric tech. The research field shows quick growth because of its superior accuracy and speed. Multiple sectors employ this technology to secure locations while also utilizing it in everyday electronic products as well as law enforcement applications.
Facial recognition tech offers secure and easy ways to check who you are. Artificial intelligence together with machine learning produce systems that achieve superior accuracy levels. This has made facial recognition more popular across different fields.
Some key uses of facial recognition tech include:
As facial recognition tech keeps getting better, we’ll see even more cool uses. The technology keeps emerging more frequently and it demands understanding of its advantages.

We think facial recognition tech could change how we handle security and identity checks. The system enables people to identify themselves through methods that are effective and simple. Our ongoing pursuit of new advancements will unlock unseen impacts that affect different spheres and everyday situations during the coming years.
| Application | Description |
|---|---|
| Security and Surveillance | Facial recognition technology is used to identify and track individuals in real-time. |
| Law Enforcement | Facial recognition technology is used to verify identities and solve crimes. |
| Consumer Electronics | Facial recognition technology is used to provide secure and convenient authentication for devices. |
We’re looking into biometric devices, focusing on iris scanning and retinal scanning. People rely on it more because these methods produce reliable and protective results. Iris scanning stands out for its ability to uniquely identify people, making it great for business security.
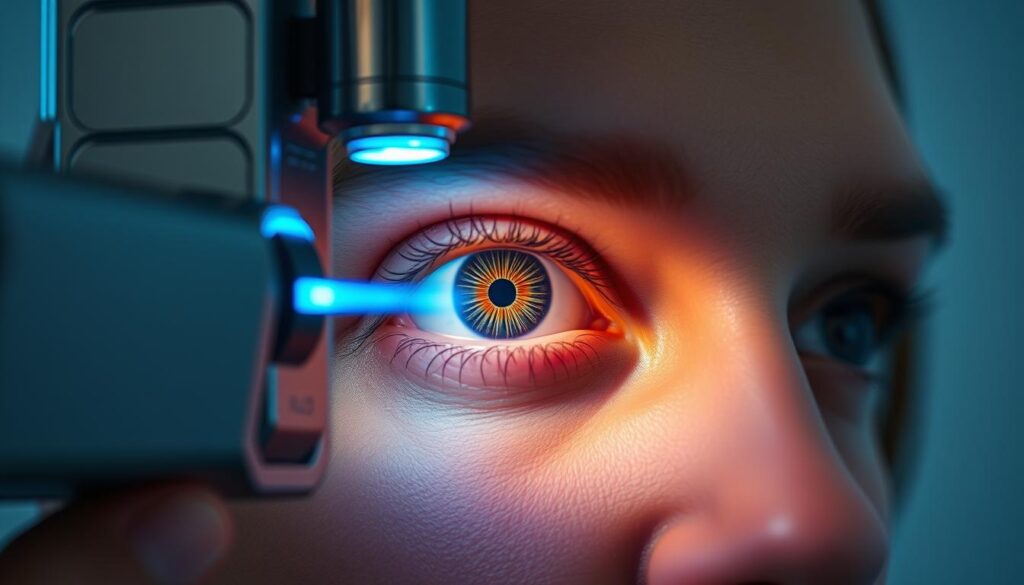
Business inspection areas need retinal scanning protection to stay secure. The system helps protect sensitive spots or information through its reliable performance.
Here are some ways it’s used:
Iris scanning is also used in personal gadgets like phones and laptops for safe unlocking. Iris scanning represents a practical method for device access which attracts numerous users because of its security features.
We’re excited to dive into voice recognition technology in biometric devices and personal security. The new technology will transform the way people handle both security operations and authentication protocols.
Voice recognition technology is easy and convenient. It lets users quickly verify their identity with biometric devices. No need for passwords or other authentication methods.
Here are some key features of voice recognition technology in biometric devices:

As we keep improving voice recognition technology, we’ll see more cool uses in personal security and biometric devices.
Exploring biometric security, we see the value of multi-factor authentication. Extra security protection results when traditional security methods unite with modern biometric systems. Users must present three authentication methods for verification such as fingerprints alongside passwords and facial recognition features. The usage of multi-factor authentication creates an extremely strong barrier against unauthorized entry.
In places where secrets are kept, like banks, biometric security is key. The system operates with passwords to authenticate access for authorized personnel to important information. The added security measures subject the system to strengthened protection which refuses identity theft while fighting cybercrime.
In the world of biometric security, multi-factor authentication adds a layer of safety for sensitive info. The system combines biological authentication with established security approaches to function. Such systems provide dependable identity verification and data protection through this method.
Setting up a biometric device right is key for its security and performance. Installation reliability depends heavily on considerations about the environment as well as network capacity and power supply. The device function will increase based on an effective setup process.
To begin the setup process the device’s compatibility with existing systems must be tested while creating security protocols for its operational framework. Implementation should follow manufacturer instructions to avoid system breakdowns. Proper planning and correct implementation can result in both secure and smooth operations of the installation.
Here are some tips for a successful biometric device installation:

By keeping these tips in mind, we can make sure the biometric device is set up right. The implementation of these tips will create both a safe and efficient method for fulfilling security requirements.
Exploring biometric devices, we must focus on data protection and privacy. Every personal security system depends on proper handling of sensitive information. Biometric data protection adds a layer of security to keep our data safe from unauthorized access.
Biometric information holds high sensitivity thus demanding complete protection. Customers should seek electronic devices that combine privacy features including encryption alongside secure storage solutions. Data protection measures enable us to minimize both data breaches and protect privacy about our details.

By focusing on biometric data protection and privacy features, we can trust our personal info is safe. As we delve into biometric devices, keeping our privacy and security top priority is key.
Investing in biometric devices raises concerns about cost. We need to examine both the equipment price during purchase along with its future worth. A detailed ROI analysis is key to understanding the financial gains.
The first phase of cost includes purchasing the equipment together with installation services and upkeep. The long-term advantages require an assessment against the initial spending costs. For example, biometric devices can cut down on the need for keys or passwords. Such cost-saving methods generate large financial benefits throughout the entire period.

Our evaluation helps us decide whether this expense brings good returns on our investment. Biometric devices offer a strong ROI. These devices deliver benefits with excellent value for everyone who uses them.
Biometric devices face challenges like technical issues, user adoption, and data security. But, there are solutions to these problems. For example, many makers of biometric devices offer help to fix technical problems.
The main difficulties companies deal with are related to making their devices more dependable and gaining user trust. Firms are spending their resources to enhance their biometric devices. They educate customers about the advantages and walkthroughs for proper device usage.
Here are some ways to solve common biometric device problems:
Knowing about biometric device challenges and solutions helps us make better choices. When picking a biometric device, think about its accuracy, reliability, and how easy it is for users to accept it.

To beat biometric device challenges, we need to stay up-to-date with new tech. This way, we can use biometric technology to keep our personal info safe and secure.
Biometric security solutions are a strong and easy way to keep our personal info safe. They include fingerprint scanners and facial recognition systems. These protective methods provide security coverage to organizations and individuals separately.
When picking a biometric security system, think about how accurate it is, how easy it is to use, and if it’s worth the cost. These factors and your needs allow you to select the most suitable security protection.
The world of biometric security is always changing. The future demands consistent attention to emerging technology along with industry patterns. This way, your chosen security stays effective and safe for a long time. Using biometric technology helps us protect our info and feel more secure in our digital world.
Today, you can find many biometric devices. These include fingerprint scanners, facial recognition tech, iris and retinal scanners, and voice recognition systems.
Biometric systems verify distinct physical or behavioral characteristics of users through advanced technology. People identify biometric systems through fingerprints as well as their face and iris patterns and voiceprint information. The system employs modern technology that performs comparisons against stored databases.
Biometric devices offer many advantages. There are more dependable because they outperform traditional passwords in accuracy. Such devices enable simple access to more secure environments.
When using fingerprint systems accuracy proves to be exceptional at reaching over 99% in identified instances. The accuracy levels vary because of both sensor technology along with environmental conditions and user conduct.
New facial recognition tech uses AI and machine learning. It’s getting better and faster. The technology finds increasing adoption in various devices alongside systems.
Retinal and iris scanners measure the precise details of your eyes for identification purposes. Your identity is verified after these images get compared by the system. The accuracy level of these systems is high yet their cost and ease of use are some limitations.
Voice recognition is becoming more popular. Users can operate this system easily because it functions with smart devices. Voice recognition proves difficult to operate successfully in loud environments.
These security systems unite rigid security features with biological identification systems. The additional protection measures increase system safety. Multiple forms of security act as strengthened barriers that delay uninvited access to your data for hackers.
When setting up biometric devices, placement and calibration are key. Biometric system setup requires risk assessments and following established safety standards.
All biometric systems require specific privacy regulations for their operation. The system uses encrypted data storage along with secure access restrictions. Security measures applied to biometric data storage protect it from unauthorized use.